You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
is there any risk.....?(AB)
- Thread starter konney
- Start date
PhilipW
Member
Yes there is. This is true of ANY device that is attached to the internet.
The ENET module uses the following port numbers:
TCP/UDP RSLinx Messaging : 44818
CIP UDP: 2222
In addition the newer 1756-ENBT also has a web server that will be open at the standard http port 80.
If you put the 1756-ENBT onto the open Ehternet you WILL have major attack problems from all the automated port scanners and DDOS bots out there.
The normal approach I use is to get some associates to set up a Linux box with two Ethernet ports and acts as a VPN/firewall/router and is configured so that only my remote PC with:
1. Its unique Ethernet MAC address
2. My unique 128bit VPN encryption hash
3. And ONLY open to the port numbers listed above.
If the box is set up by someone you trust then it will 100% secure for all practical purposes.
The ENET module uses the following port numbers:
TCP/UDP RSLinx Messaging : 44818
CIP UDP: 2222
In addition the newer 1756-ENBT also has a web server that will be open at the standard http port 80.
If you put the 1756-ENBT onto the open Ehternet you WILL have major attack problems from all the automated port scanners and DDOS bots out there.
The normal approach I use is to get some associates to set up a Linux box with two Ethernet ports and acts as a VPN/firewall/router and is configured so that only my remote PC with:
1. Its unique Ethernet MAC address
2. My unique 128bit VPN encryption hash
3. And ONLY open to the port numbers listed above.
If the box is set up by someone you trust then it will 100% secure for all practical purposes.
PhilipW
Member
The answer depends on the switch. You have not included any information on the model of the switch and how you think it will be configured. There are many different types of switch and levels of functionality.
Some advanced switches can be configured to perform the highly secure VPN connection that I described in my last post. But many cannot.
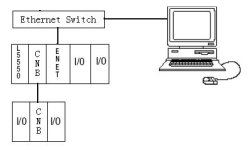
In most cases I would NOT use the system in that you have shown in the drawing you have posted as the switch would most likely expose the CPU to the Internet.
You really should seek local advice from someone who specialises in systems networking and KNOWS about security because there are many details that have to be considered.
Some advanced switches can be configured to perform the highly secure VPN connection that I described in my last post. But many cannot.
In most cases I would NOT use the system in that you have shown in the drawing you have posted as the switch would most likely expose the CPU to the Internet.
You really should seek local advice from someone who specialises in systems networking and KNOWS about security because there are many details that have to be considered.
Bitmore
Member
Well actually no.
Sorry to upset the apple cart.
From all the years of experience, tons of hardware, and miles of cat5 cable......
You have little to worry about stuph like that.
Try this and confirm it for yourself!
Connect to the PLC or Versaview or what ever device you have on an industrial ethernet, now click on your ICON for the internet,,,,
did you connect?
oh well...let us know
I am sure the IT guys have a handle on this, and you have asked a VALID question. It is up to them (the guys that set up the company network) to worry about that, and besides if you choose the right address it cannot be sent out or accessed from the internet (un-routable).
a gateway address of 255.255.255.0 comes to mind.
Sorry to upset the apple cart.
From all the years of experience, tons of hardware, and miles of cat5 cable......
You have little to worry about stuph like that.
Try this and confirm it for yourself!
Connect to the PLC or Versaview or what ever device you have on an industrial ethernet, now click on your ICON for the internet,,,,
did you connect?
oh well...let us know
I am sure the IT guys have a handle on this, and you have asked a VALID question. It is up to them (the guys that set up the company network) to worry about that, and besides if you choose the right address it cannot be sent out or accessed from the internet (un-routable).
a gateway address of 255.255.255.0 comes to mind.
Last edited:
hello,guys~!
i thought it over and felt that i had stuck in the mud.maybe there is no need to care this myself and i should hand the security problem to those specialist in system networking.but i still want to know that whether the CPU will be harmed if the enbt module is under the attack.
i thought it over and felt that i had stuck in the mud.maybe there is no need to care this myself and i should hand the security problem to those specialist in system networking.but i still want to know that whether the CPU will be harmed if the enbt module is under the attack.
kamenges
Member
I think this is a two or maybe three part question.
If the ENET is connected to the Internet it is open to attack. However, do you have any reason to believe someone would want to? I think you can approach this kind of like a safety risk assessment. Is there a risk, how likely is the risk (how much exposure) and what are the consequences of a problem.
Most of the viruses and other software bugs out there are based on exploiting a hole in a popular operating system or program. So most of those are not a threat to your ENET card. Now you are limited to an actual hacker actively trying to get into the plc. First of all, why would they want to? Most of these social deviants are trying to wipe out bank accounts and shut down "the government". Why would they mess with your plc? The return just isn't there for them. Also, how bad would it be for you if someone did get in and scrambled your program? Could you just cycle power, reload the program and go again or would the downtime cost you serious money. Is a fault a safety concern?
You also need to decide how serious a threat you are trying to repel. If you just want to keep out the casual pest a simple password solution might be enough. If you want to try to keep out real serious hackers your solution will need to be more complex.
Your answers to these questions might steer you toward how you want to proceed.
Keith
If the ENET is connected to the Internet it is open to attack. However, do you have any reason to believe someone would want to? I think you can approach this kind of like a safety risk assessment. Is there a risk, how likely is the risk (how much exposure) and what are the consequences of a problem.
Most of the viruses and other software bugs out there are based on exploiting a hole in a popular operating system or program. So most of those are not a threat to your ENET card. Now you are limited to an actual hacker actively trying to get into the plc. First of all, why would they want to? Most of these social deviants are trying to wipe out bank accounts and shut down "the government". Why would they mess with your plc? The return just isn't there for them. Also, how bad would it be for you if someone did get in and scrambled your program? Could you just cycle power, reload the program and go again or would the downtime cost you serious money. Is a fault a safety concern?
You also need to decide how serious a threat you are trying to repel. If you just want to keep out the casual pest a simple password solution might be enough. If you want to try to keep out real serious hackers your solution will need to be more complex.
Your answers to these questions might steer you toward how you want to proceed.
Keith
rsdoran
Lifetime Supporting Member
For me there was not enough information included. Using an Ethernet adapter means you are using Ethernet for communications....not that it will be attached to the internet. The plc could be setup on an internal LAN that may or may not be accessible by the internet, either way if on a LAN the odds of an attack are minimal if at all.
This may be of interest:
http://domino.automation.rockwell.c...B6EBC4159EA55FE985256B8200610597?OpenDocument
This may be of interest:
http://domino.automation.rockwell.c...B6EBC4159EA55FE985256B8200610597?OpenDocument
PhilipW
Member
I mostly agree with the comments made by rsdoran and kamenges. Almost all of the time us PLC guys can assume that we can achieve Internet security "by obscurity", ie not all that many hackers would either know of or be interested in our systems.
BUT early last year I was involved in a water demineralising plant project that was part of a significant power generatiing plant. The interesting aspect was the utterly anal attitude of the project principals toward allowing any remote access via the internet. Nothing I suggested was acceptable, not even the completely bullet-proof scheme I outlined in my first post..
A very frustrating and expensive proposition because it took an extra THREE months being present on site over what was desirable because they would not let me go home during the very extended plant acceptance trials. (And we didn't get paid for it in the end either!!)
Understanding however came very late in the piece when I realised that the USA based principal was directly part of the same organisation that was running the controls system whose alarming SCADA failed to detect the incipient overloading that lead to the infamous NorthEast blackout of a few years ago.
Two further points:
1. The 1756-ENBT has an http web server on port 80. How vulnerable is this to Denial of Service attack?
2. Also we have only answered konney's original question in terms of an attack on the PLC CPU, which I agree is very remote. But what about any PC based SCADA/HMI that is very likely to on the same network?
BUT early last year I was involved in a water demineralising plant project that was part of a significant power generatiing plant. The interesting aspect was the utterly anal attitude of the project principals toward allowing any remote access via the internet. Nothing I suggested was acceptable, not even the completely bullet-proof scheme I outlined in my first post..
A very frustrating and expensive proposition because it took an extra THREE months being present on site over what was desirable because they would not let me go home during the very extended plant acceptance trials. (And we didn't get paid for it in the end either!!)
Understanding however came very late in the piece when I realised that the USA based principal was directly part of the same organisation that was running the controls system whose alarming SCADA failed to detect the incipient overloading that lead to the infamous NorthEast blackout of a few years ago.
Two further points:
1. The 1756-ENBT has an http web server on port 80. How vulnerable is this to Denial of Service attack?
2. Also we have only answered konney's original question in terms of an attack on the PLC CPU, which I agree is very remote. But what about any PC based SCADA/HMI that is very likely to on the same network?
rsdoran
Lifetime Supporting Member
Thats why I said not enough info was given. The use of Ethernet doesnt necessarily mean internet connection. If a plc or hmi/scada PC is connected via Ethernet to an internal LAN then an internet attack is unlikely.
If the system will be attached to an internet connection then approriate measures should be taken...ie firewall, VPN, passwords etc to minimise the chances of Denial of Service etc type attacks.
If the system will be attached to an internet connection then approriate measures should be taken...ie firewall, VPN, passwords etc to minimise the chances of Denial of Service etc type attacks.
Similar Topics
Hello
Im an Controls Engineer that has been asked to supervise some projects.
Im new into this and suddenly everybody is talking about risk...
- Replies
- 1
- Views
- 1,453
Good Afternoon,
We have a light curtain system that momentarily see's that it is blocked.
Is there an adjustment that you can delay ...
- Replies
- 8
- Views
- 2,291
Everyone says I need to perform a risk assessment before any job or controls planning. Is there a place to find the right way of "how to"?'
From...
- Replies
- 4
- Views
- 1,704
I'm trying to get a better handle on safety standards, but the more I read the more lost I feel.
Being a US machine standard, you would think...
- Replies
- 7
- Views
- 2,651
Good Morning ,
Do you folks know of any engineering firms in Virginia that do Arc Flash Assessments ? We have recently received some new...
- Replies
- 4
- Views
- 2,672