lunenburger
Member
Does anyone know why Rockwell has changed the way they do their ethernet configuration?
For years we used 2 ENBT modules, one to connect to our plantwide PLC network. And one to connect all the VFD's and device level I/O.
Now Rockwell is suggesting to put a ring inside the panel with a 1783-ETAP connecting all the drives, PLC, PanelView, and connection to our PLC network.
(see pic)
The issue I see with this is that I can now ping the VFD's and servo controller from our programming computer which makes me nervous....
As far as I can see there is no way to partition an ETAP, and the Rockwell rep doing the installation doesn't recommend using an ENBT????
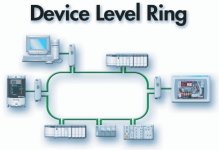
For years we used 2 ENBT modules, one to connect to our plantwide PLC network. And one to connect all the VFD's and device level I/O.
Now Rockwell is suggesting to put a ring inside the panel with a 1783-ETAP connecting all the drives, PLC, PanelView, and connection to our PLC network.
(see pic)
The issue I see with this is that I can now ping the VFD's and servo controller from our programming computer which makes me nervous....
As far as I can see there is no way to partition an ETAP, and the Rockwell rep doing the installation doesn't recommend using an ENBT????





