Hi,
I created this post recently and got some great information:
http://www.plctalk.net/qanda/showthread.php?t=127080
One thing I'm trying to find out though is what are the pros and cons when using a fiber network and set up with dividing 1 VLAN into separate subnets for each area / line / cell VS dividing it into separate VLANs per area / line / cell?
So far I think the pros for multiple VLANs are:
- Can have duplicate IP addresses in the factory - that are on separate VLANs by using a NAT switch. This is great so we can have a closed system without worrying about IP clashes, but also if we have two or more identical lines then PLC projects can match, including IPs. Question: Can we do this without separate VLANs and just using subnets + NAT?
- Security - If one VLAN is compromised it is much harder for a hacker to get onto the other VLANs. Is this true?
- Scalability - a VLAN can have many more devices connected than a subnet.
- Reliability - I'm assuming it's better to have servos and robots, etc connected to 1 VLAN per line rather than every device on the factory floor to 1 VLAN across the factory? This seems one of the most important points, as we don't want the network design to create device issues. Is this important? And if all devices on the factory floor were connected to 1 VLAN with different subnets could we get any servo / device issues? Thinking about this, if we had a device on the system that was creating excess demand due to a fault, would that not bring down the whole VLAN stopping the whole factory? If it were split into separate VLANs it would only bring down the VLAN it was on, and the rest would be okay?
The only cons I can see for using multiple VLANs are:
- complicated, and the need for controls engineers that understand networking well, and how the set up across VLANs works.
Pros for using subnets:
- easier to understand and connect to the factory network
Cons for using subnets:
- device limit could be hit
- firewalls needed between each subnet if want similar security to separate VLANs method
- if problem device on network, it could bring down the whole factory
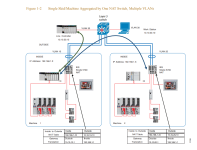
The diagram below is the best example I've seen on how to set this up.
It is from this document:
https://literature.rockwellautomatio...d007_-en-p.pdf
Thanks
I created this post recently and got some great information:
http://www.plctalk.net/qanda/showthread.php?t=127080
One thing I'm trying to find out though is what are the pros and cons when using a fiber network and set up with dividing 1 VLAN into separate subnets for each area / line / cell VS dividing it into separate VLANs per area / line / cell?
So far I think the pros for multiple VLANs are:
- Can have duplicate IP addresses in the factory - that are on separate VLANs by using a NAT switch. This is great so we can have a closed system without worrying about IP clashes, but also if we have two or more identical lines then PLC projects can match, including IPs. Question: Can we do this without separate VLANs and just using subnets + NAT?
- Security - If one VLAN is compromised it is much harder for a hacker to get onto the other VLANs. Is this true?
- Scalability - a VLAN can have many more devices connected than a subnet.
- Reliability - I'm assuming it's better to have servos and robots, etc connected to 1 VLAN per line rather than every device on the factory floor to 1 VLAN across the factory? This seems one of the most important points, as we don't want the network design to create device issues. Is this important? And if all devices on the factory floor were connected to 1 VLAN with different subnets could we get any servo / device issues? Thinking about this, if we had a device on the system that was creating excess demand due to a fault, would that not bring down the whole VLAN stopping the whole factory? If it were split into separate VLANs it would only bring down the VLAN it was on, and the rest would be okay?
The only cons I can see for using multiple VLANs are:
- complicated, and the need for controls engineers that understand networking well, and how the set up across VLANs works.
Pros for using subnets:
- easier to understand and connect to the factory network
Cons for using subnets:
- device limit could be hit
- firewalls needed between each subnet if want similar security to separate VLANs method
- if problem device on network, it could bring down the whole factory
The diagram below is the best example I've seen on how to set this up.
It is from this document:
https://literature.rockwellautomatio...d007_-en-p.pdf
Thanks

Last edited:



