You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
How to Allen Bradley get PLCs onto the corporate network without RS-Linx Gateway?
- Thread starter Dayvieboy
- Start date
TheWaterboy
Lifetime Supporting Member + Moderator
1. WHY? Best practice is to keep the PLCs completely Off the corporate network.
2. Get IT involved. You put a bunch of PLC's on a corporate network and they will not be amused.
3. PLC's dont like a chatty network like a corporate lan.
4. It's a bad idea
If instead you are staying within the OT segment and just need secure routing to remote devices, you are going to need hardware and expertise.
2. Get IT involved. You put a bunch of PLC's on a corporate network and they will not be amused.
3. PLC's dont like a chatty network like a corporate lan.
4. It's a bad idea
If instead you are staying within the OT segment and just need secure routing to remote devices, you are going to need hardware and expertise.
Ken Roach
Lifetime Supporting Member + Moderator
What you are describing is exactly what NAT appliances are designed to do. $700 - 1000 per network isn't unreasonable for something with a 24V power supply that mounts on a DIN rail.
If you're on a super-restricted budget but have some networking skills, you could use a $40 travel router running OpenWRT for the same sort of NAT functions. Or put a little extra professionalism into it and buy a case of Ubiquiti Edgerouter X units and install one at each site.
Or, if your budget is just the aggravation of teaching remote users about networking, enable routing in the Windows 10 Registry Editor, open up TCP Port 44818 in the firewall, and teach your users how to enter static routes at the command line. Or, get adventurous and install a software NAT on those Windows PC's.
If you're on a super-restricted budget but have some networking skills, you could use a $40 travel router running OpenWRT for the same sort of NAT functions. Or put a little extra professionalism into it and buy a case of Ubiquiti Edgerouter X units and install one at each site.
Or, if your budget is just the aggravation of teaching remote users about networking, enable routing in the Windows 10 Registry Editor, open up TCP Port 44818 in the firewall, and teach your users how to enter static routes at the command line. Or, get adventurous and install a software NAT on those Windows PC's.
Last edited:
TheWaterboy
Lifetime Supporting Member + Moderator
I can hear SecOps grinding their teeth . . 
Ken Roach
Lifetime Supporting Member + Moderator
I have a "PLC lab" in my office, with a menagerie of controllers, HMIs, servos, and computers. To keep it convenient to connect to both ordinary network and internet resources as well as the lab, I have a small old mini server computer running OpenWRT, the Linux-based router software. Even though it's meant to run WiFi access devices, it gurgles along happily as a wired two-port router and firewall. This allows me to keep all of my automation devices and traffic off the corporate LAN.
When my IT department noticed some impermissible traffic (DropBox... it's a long story) they couldn't find my router from the corporate network side. It didn't respond to PINGs, wasn't using normal administrative TCP ports, and randomized its MAC address. It was both very polite and secure, and from their perspective looked *exactly* like an espionage tool. But they were able to figure out which IP address it used, and locked it down before going around offices looking at every patch panel to see if there was something sneaky in place. We had a lengthy discussion about not attaching our home PCs even to isolated networks before I was allowed to use my lab again.
If I am going to "not get IT involved" I am going to want a simple device I can administer myself. A-B or Moxa or Phoenix Contact or Red Lion routers all fit the bill, but so do Ubiquiti EdgeRouters or OpenWRT boxes. The EdgeRouter X is sixty bucks and has a low risk of Chinese malware coming preinstalled.
When my IT department noticed some impermissible traffic (DropBox... it's a long story) they couldn't find my router from the corporate network side. It didn't respond to PINGs, wasn't using normal administrative TCP ports, and randomized its MAC address. It was both very polite and secure, and from their perspective looked *exactly* like an espionage tool. But they were able to figure out which IP address it used, and locked it down before going around offices looking at every patch panel to see if there was something sneaky in place. We had a lengthy discussion about not attaching our home PCs even to isolated networks before I was allowed to use my lab again.
If I am going to "not get IT involved" I am going to want a simple device I can administer myself. A-B or Moxa or Phoenix Contact or Red Lion routers all fit the bill, but so do Ubiquiti EdgeRouters or OpenWRT boxes. The EdgeRouter X is sixty bucks and has a low risk of Chinese malware coming preinstalled.
Dayvieboy
Lifetime Supporting Member
The IT network is probably not the correct term, it is the SCADA network and 100% isolated from the front office IT. We also have VLAN separations.1. WHY? Best practice is to keep the PLCs completely Off the corporate network.
2. Get IT involved. You put a bunch of PLC's on a corporate network and they will not be amused.
3. PLC's dont like a chatty network like a corporate lan.
4. It's a bad idea
If instead you are staying within the OT segment and just need secure routing to remote devices, you are going to need hardware and expertise.
Dayvieboy
Lifetime Supporting Member
I am just trying to emulate what RS-Linx Gateway software does without the licenses.I can hear SecOps grinding their teeth . .
RS-Linx Gateway has been on the network forever to develop PLCs networks remote from the PLC lab.
Our PLC network was THE only facility out of 5 to not be affected by a serious ransom ware attack.
The attack seriously hobbled the 4 other locations for weeks and had repercussion for months after on both IT and OT networks.
IT/OT separation is audited annually by 3rd party consultants, and they are pretty thorough.
Dayvieboy
Lifetime Supporting Member
Money is not the issue; we are building tools that are in different clean rooms with the PLCs on different subnets.What you are describing is exactly what NAT appliances are designed to do. $700 - 1000 per network isn't unreasonable for something with a 24V power supply that mounts on a DIN rail.
If you're on a super-restricted budget but have some networking skills, you could use a $40 travel router running OpenWRT for the same sort of NAT functions. Or put a little extra professionalism into it and buy a case of Ubiquiti Edgerouter X units and install one at each site.
Or, if your budget is just the aggravation of teaching remote users about networking, enable routing in the Windows 10 Registry Editor, open up TCP Port 44818 in the firewall, and teach your users how to enter static routes at the command line. Or, get adventurous and install a software NAT on those Windows PC's.
One rule is that hardware that will not ship with the tool should generally not be in that clean room.
Everything should be built to POR (Plan of Record), with few exceptions.
No extra power supplies, Din rail, NAT, Router, Switch etc.
Tools are wire gapped when installed on the customer site.
Having extra hardware that does nothing on the final design would require a request for exemption and an engineering justification report to be filed,
and then after waiting months it may or may not be approved.
The mere thought of the **** storm of e-mails that would be created by me sending out such a proposal is just not worth it.
A RS-Linx Gateway software replacement is all that I am looking for.
It is pretty much a software NAT packaged in RS-Linx from what I can tell.
You are pretty on target on the budget goal, teaching/learning about networking.
Say we have 10 programmers on 1 tool.
Current design has 10 VMs with 10 Studio5000 Professional licenses on every tool.
Developers' Remote desktop into their own VM on every tool.
VM access is password controlled and during experiments, access is denied.
This leaves up to 10 Studio 5000 licenses locked in the clean room until the experiment is over or borrowed time expires.
USB ports are disabled except for mouse and keyboard drivers, so you cannot retrieve licenses that way.
Rockwell's paperwork license method is no fun either.
If we get a software NAT to work, we can develop with our PLC lab licenses and not need 10 extra for the clean room.
Along with keeping all 10 extra VMs up to date on firmware, AOIs, EDSs, AOPs
As always, Thanks for the input, I will look into the Windows 10 registry route.
Ken Roach
Lifetime Supporting Member + Moderator
I admit that your level of sophistication and budget is not what I expected when I first read your post. Thank you for the context and detail.
RSLinx Gateway was built to allow access over TCP/IP networks to hardware drivers like DH485, DH+, and ControlNet that were running on proprietary interface cards and modules. It is not a "NAT" or "router" in any technically meaningful way, but rather a way to transport RSLinx functions across a TCP/IP network where they can be executed by an instance of a hardware driver.
Because it will do that same function when the local driver is an AB_ETH or ETHIP driver instead of an ISA or PCI or USB device, you can essentially use it as a "remote NIC" where your TCP/IP connection comes to the pictured PC on one network, and the automation connection to the PLCs is on another physical and logical network.
Simply opening up a port on the Windows Firewall, enabling TCPIP Routing, and teaching your engineers how to configure static routes at the command line would be one way to accomplish your goal. I don't think it's very secure, though you could mitigate a good deal of the risk by limiting the firewall exception to TCP Port 44818.
I'm curious about your VM use, and I'm not sure I understand it. Are the pictured Dell PCs in each workcell running a hypervisor with a Windows VM that has the engineering tools on it, and they're air-gapped from the yellow NIC#1 networks during controlled cleanroom experiments ? Which hypervisor are you using; Microsoft Hyper-V, VirtualBox, VMWare Workstation, or something else ? What OS is on those computers ?
Do your engineers accessing the "PLC Lab" use virtual machines there, or do they have Studio 5000 loaded on their ordinary bare-metal desktops operating systems on their workstations, whether in the shop or over VPN ?
It's entirely possible that the Windows Remote Access and Management Tools will do what you want, but that takes me out of my comfort zone with PC networking that isn't done in a little box with a power plug.
A RS-Linx Gateway software replacement is all that I am looking for.
It is pretty much a software NAT packaged in RS-Linx from what I can tell.
RSLinx Gateway was built to allow access over TCP/IP networks to hardware drivers like DH485, DH+, and ControlNet that were running on proprietary interface cards and modules. It is not a "NAT" or "router" in any technically meaningful way, but rather a way to transport RSLinx functions across a TCP/IP network where they can be executed by an instance of a hardware driver.
Because it will do that same function when the local driver is an AB_ETH or ETHIP driver instead of an ISA or PCI or USB device, you can essentially use it as a "remote NIC" where your TCP/IP connection comes to the pictured PC on one network, and the automation connection to the PLCs is on another physical and logical network.
Simply opening up a port on the Windows Firewall, enabling TCPIP Routing, and teaching your engineers how to configure static routes at the command line would be one way to accomplish your goal. I don't think it's very secure, though you could mitigate a good deal of the risk by limiting the firewall exception to TCP Port 44818.
I'm curious about your VM use, and I'm not sure I understand it. Are the pictured Dell PCs in each workcell running a hypervisor with a Windows VM that has the engineering tools on it, and they're air-gapped from the yellow NIC#1 networks during controlled cleanroom experiments ? Which hypervisor are you using; Microsoft Hyper-V, VirtualBox, VMWare Workstation, or something else ? What OS is on those computers ?
Do your engineers accessing the "PLC Lab" use virtual machines there, or do they have Studio 5000 loaded on their ordinary bare-metal desktops operating systems on their workstations, whether in the shop or over VPN ?
It's entirely possible that the Windows Remote Access and Management Tools will do what you want, but that takes me out of my comfort zone with PC networking that isn't done in a little box with a power plug.
Dayvieboy
Lifetime Supporting Member
Good reminder, the early 90's when you had a $ 1,200 KTX card in an ISA slot,
or worse yet, the PCMCIA PCK card of which I still have a few in my box of treasures.
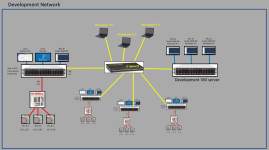
Here is a diagram of a more accurate depiction of what I am working with.
Each programmer logs into their own Studio5000 VM from home or office, each VM has a Studio5000 pro license.
Each machine has its own VM server that ships with the machine with 3 VMs.
We have ~ 10 programmers and ~ 6 or 7 machines being built at any one time.
Machine will be air gapped when installed at the customer site.
Studio5000 service edition is installed for field troubleshooting on air gapped tool. (upload/download/view code only)
I am looking into opening the port and trying that approach.
Purchasing a few copies of Rs-Linx Gateway may be the easy out.
I see you are up in Seattle area.
I spent 9 months @ Pyramid Brewery in Berkeley California on the start-up in 1996.
They asked me to do some work at the Seattle Facility. Did a few upgrades.
Then they paid to do a study on what it would take to bring the Seattle location up to speed.
Based on my report (and several other factors) they shut down the production facility there and moved production to Portland I believe.
Though I think they put a small home brew apparatus on campus for tax reasons of some sort.
Also worked at Atlas Casting (now Americast) kind of dirty in the plant, but they really build some cool stuff.
Worked @ Metagenics in Gig Harbor several times.
or worse yet, the PCMCIA PCK card of which I still have a few in my box of treasures.
Here is a diagram of a more accurate depiction of what I am working with.
Each programmer logs into their own Studio5000 VM from home or office, each VM has a Studio5000 pro license.
Each machine has its own VM server that ships with the machine with 3 VMs.
We have ~ 10 programmers and ~ 6 or 7 machines being built at any one time.
Machine will be air gapped when installed at the customer site.
Studio5000 service edition is installed for field troubleshooting on air gapped tool. (upload/download/view code only)

I am looking into opening the port and trying that approach.
Purchasing a few copies of Rs-Linx Gateway may be the easy out.
I see you are up in Seattle area.
I spent 9 months @ Pyramid Brewery in Berkeley California on the start-up in 1996.
They asked me to do some work at the Seattle Facility. Did a few upgrades.
Then they paid to do a study on what it would take to bring the Seattle location up to speed.
Based on my report (and several other factors) they shut down the production facility there and moved production to Portland I believe.
Though I think they put a small home brew apparatus on campus for tax reasons of some sort.
Also worked at Atlas Casting (now Americast) kind of dirty in the plant, but they really build some cool stuff.
Worked @ Metagenics in Gig Harbor several times.
Similar Topics
I have a client who periodically experiences network communication issues. Sometimes when I VPN into the site, their SCADA systems will flash comm...
- Replies
- 2
- Views
- 178
Hello guys,
iam planning to switch from Allen-Bradley PLCs to B&R PLCs.
Does anyone of you know if its possible to import the Logic in...
- Replies
- 2
- Views
- 1,564
Hey guys,
I'm working on a proposal for a client, and long story short I need to suggest a new master PLC for polling existing RTU sites that are...
- Replies
- 23
- Views
- 9,790
Hello everyone,
I have 3 identical processes controlled by 3 Allen Bradley PLCs (1769-L33ER CompactLogix 5370). All 3 share some identical...
- Replies
- 13
- Views
- 3,292
Good morning,
Recently, I've heard the Micrologix 1500 PLC has become obsolete and Allen Bradley does not repair them either.
Is there a list...
- Replies
- 8
- Views
- 2,583



